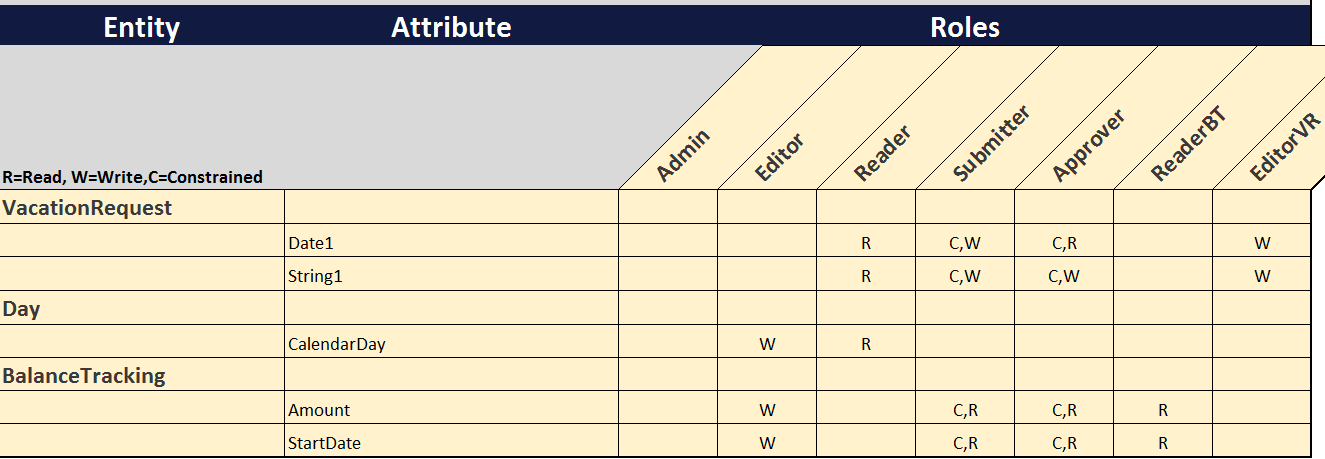
“With SAP tools like Fiori and UI5, why would I need Mendix?”
As a practitioner who directs our architecture and development of Mendix applications alongside SAP developers, I get asked this question a lot. Rapid Application Development (RAD) tools like Mendix are on the rise because as businesses begin their journey into digital transformation, they realize that the agility necessary to respond to rapidly changing competition and value perceptions require focused teams that combine business leadership and IT to design and deploy solutions just as rapidly. Waiting for a waterfall, stack-developed project to get scoped and developed will typically miss the mark, come out behind the curve of the transformation, and be dead in the water by the time it hits the market or the business.